DNS In General
DNS Server
All DNS servers fall into one of four categories:
- Recursive Resolvers
- Root Nameservers
- TLD Nameservers
- Authoritative Nameservers
A recursive resolver (also known as a DNS recursor) is almost always the first stop in a DNS query. The recursive resolver acts as a middleman between a client and a DNS nameserver.
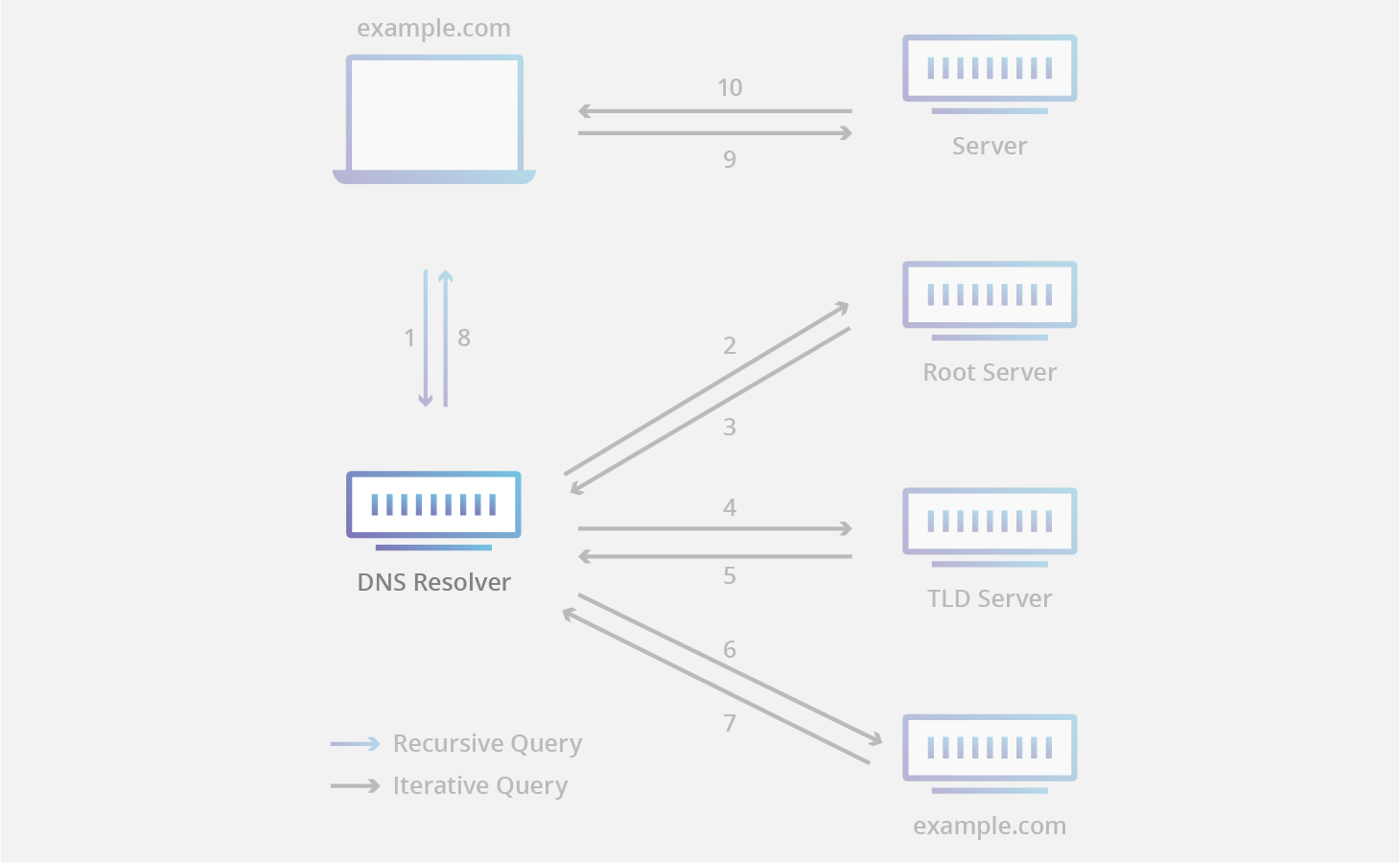
cc @ https://www.cloudflare.com/learning/dns/dns-server-types/
DNS primarily uses
UDPon port number53to serve requests. DNS queries consist of a singleUDPrequest from the client followed by a singleUDPreply from the server. When the length of the answer exceeds 512 bytes and both client and server supportEDNS, largerUDPpackets are used. Otherwise, the query is sent again using theTCP.TCPis also used for tasks such as zone transfers. Some resolver implementations useTCPfor all queries.
DNS Messages
The DNS protocol uses two types of DNS messages, queries and replies, and they both have the same format. Each message consists of,
- a header
Identification(used to match responses with queries)Flags- a single bit which indicates if the message is a query (0) or a reply (1)
- four bits indicating the type of query, or the type of query this message is a response to. 0 is a standard query, 1 is an inverse query, 2 is a server status request.
- a single-bit indicates if the DNS server is authoritative for the queried hostname
- a single-bit indicates if the client wants to send a recursive query (“RD”).
- a single-bit indicates if the replying DNS server supports recursion (“RA”), as not all DNS servers are configured to do this task.
- ?-bit indicates if the message was truncated for some reason (“TC”)
- four-bit is used for error codes
- Number of
questions - Number of
answers - Number of
authority Resource Records (RRs) - Number of
additional Resource Records (RRs)
- and four sections:
question: has the domain name and type of record being resolved; eachlabelis prefixed by the length of thatlabel.answer: has the resource records of the queried name.authority- an additional space
Type Of Record
Arecord - The record that holds the IP address of a domain.CNAMErecord - Forwards one domain or subdomain to another domain, does NOT provide an IP address.TXTrecord - Lets an admin store text notes in the record.NSrecord - Stores the name server for a DNS entry.SOArecord - Stores admin information about a domain. The “start of authority” record can store important info about the domain such as the email address of the administrator, when the domain was last updated, and how long the server should wait between refreshes.SRVrecord - Specifies a port for specific services. Ex.[@_sip._tcp.example.com.] [SRV] [8080 example2.com] [TTL],_sipindicates the type of service,_tcpindicates the protocol, and8080indicates the port.PTRrecord - Provides a domain name in reverse-lookups, which return the domain associated with a given IP address.
Resource Record
| Field | Description | Length (octets) |
|---|---|---|
| NAME | Name of the node to which this record pertains. @ is a placeholder used to represent “the current domain” without any www or sub-domain name. |
Variable |
| TYPE | Type of RR in numeric form (e.g., 15 for MX RRs) | 2 |
| CLASS | Class code, basically IN |
2 |
| TTL | Count of seconds that the RR stays valid (The maximum is 231−1, which is about 68 years) | 4 |
| RDLENGTH | Length of RDATA field (specified in octets) | 2 |
| RDATA | Additional RR-specific data | Variable, as per RDLENGTH |
Label
aaaaaa.bbbbbb.cccccc
--^-- --^-- --^--
label label label
A label may contain zero to 63 characters. The null label, of length zero, is reserved for the root zone.
DNS Setting In Linux (Ubuntu)
/etc/resolv.conf
-
nameserver: at most 3 IP address. For multiple servers, the resolver library queries them in the order listed. The algorithm used here is,- try first nameserver
- if the query times out, try next
- … until finish all (up to) 3 nameservers
- if the maximum number of retries have made, stop; else go back to step 1
-
search: Search list for host-name lookup. By default, it contains only the local domain name, ex,my-mac.my-domain. Query having w/o.(dot)in it will be attempted using each component of the search path in turn until a match is found. The search list is limited to six domains. -
options:ndots: sets a threshold for the number of dots which must appear in a name given to before an initial absolute query will be made. The default for n is 1, meaning that if there are any dots in a name, the name will be tried first as an absolute name before anysearchlist elements are appended to it. Ex. Queryexample.comwill be firstly send before searching forexample.com.my-mac.my-domain.
Dnsmasq
Comes with the stock Ubuntu 16.04.
To find the dnsmasq config,
ps -ef | grep dnsmasq
#/usr/sbin/dnsmasq --no-resolv --keep-in-foreground --no-hosts --bind-interfaces --pid-file=/var/run/NetworkManager/dnsmasq.pid --listen-address=127.0.1.1 --cache-size=0 --conf-file=/dev/null --proxy-dnssec --enable-dbus=org.freedesktop.NetworkManager.dnsmasq --conf-dir=/etc/NetworkManager/dnsmasq.d
To see NetworkManager managed DHCP and DNS info,
nmcli d show enp0
^
*your major NIC*
Detailed info of dnsmasq,
man dnsmasq
Ways To Override DNS Conf
dhcp.conf
If use DHCP to get the dynamic IP.
#/etc/dhcp/dhcp.conf
supersede domain-name-servers 1.1.1.1,8.8.8.8,8.8.4.4;
resolv.conf
#/etc/resolv.conf
nameserver 1.1.1.1
dnsmasq.d
echo 'server=1.1.1.1' > /etc/NetworkManager/dnsmasq.d/use-cloudflare-dns
systemctl restart NetworkManager
Reverse lookup
For example, assuming the IPv4 address
208.80.152.2is assigned to Wikimedia, it is represented as a DNS name in reverse order:2.152.80.208.in-addr.arpa. When the DNS resolver gets a pointer (PTR) request, it begins by querying the root servers, which point to the servers of American Registry for Internet Numbers (ARIN) for the208.in-addr.arpazone. ARIN’s servers delegate152.80.208.in-addr.arpato Wikimedia to which the resolver sends another query for2.152.80.208.in-addr.arpa, which results in an authoritative response.
DDNS
Clients can notify their respective DNS server of the updated IP address they had received from a DHCP server or through self-configuration.
If we use a single, combined DNS+DHCP solution which can maintain the consistency between both tables by itself, there’s no need to enable DDNS.
Else, we need to either,
- enable DDNS for clients notifying DNS server with the new IP address allocated by DHCP server, or,
- let DHCP server to notify DNS server the new assignments directly
DNS In Docker
For containers NOT using default bridge network, Dockerd will config DNS in the container as,
-
There’s an embedded DNS server handling all DNS queries from containers (also for inter-container name resolving)
-
If no config flag, docker use filtered host’s
/etc/hostsand/etc/resolv.conf. Fliter will eliminatelocalhostunreachables, likenameserver 127.0.1.1. Since127.0.0.0/8of host can’t be accessed within containers except for--network=host. If empty after filtered,8.8.8.8is added by default -
Both
/etc/hostsand/etc/resolv.confinside the container are managed by Dockerd. So, to change the config, usedocker run --[flags]instead of editing the files inside the container or using mount. -
Flag
--dns. The IP address of a DNS server.- For multiple DNS servers, use multiple flags
container:/etc/resolv.confwill always be127.0.0.11which will not be effected by this flag- Instead, input value of
--dnsis keeped and used by the embedded DNS server to forward the DNS query if embedded DNS server is unable to resolve a name resolution request from the containers - If you need access to the host’s
localhostresolver (likednsmasq), modify DNS service on the host to listen on a non-localhost address which is reachable within the container. (^stackoverflow)
-
Flag
--dns-search. A DNS search domain to search non-fully-qualified hostnames- For multiple DNS search prefixes, use multiple flags
-
Flag
--hostname. The hostname a container uses for itself. Defaults to the container’s ID if not specified
DNS In K8s
https://kubernetes.io/docs/tasks/administer-cluster/dns-custom-nameservers/
CoreDNS
https://coredns.io/manual/toc/
Be aware that CoreDNS does NOT have a native recursive resolver. ^
Service Discovery
DNS can be use for service discovery by,
- Using
SRVrecords in DNS as database and, - Service actively send DDNS request to DNS to update the
SRVrecord.
However, DNS-SD also have cons:
- Uncontrolled TTLs
- Delay between the moment a node failure is detected and the moment the clients execute their DNS service discovery queries
- while most JSON/REST implementations use long-polling mechanisms to trigger updates on the clients instantaneously
Build Your Own Dns Server
Be aware if the DNS has looped dependencies.
Ref.
- https://docs.docker.com/v17.09/engine/userguide/networking/configure-dns/
- https://en.wikipedia.org/wiki/Domain_Name_System
- https://ns1.com/resources/dns-protocol
- https://linux.die.net/man/5/resolv.conf
- https://www.cloudflare.com/learning/dns/dns-server-types/
- https://tools.ietf.org/html/rfc1035
- https://en.wikipedia.org/wiki/Dynamic_DNS
- https://www.haproxy.com/blog/dns-service-discovery-haproxy/
- https://en.wikipedia.org/wiki/Multicast_DNS
- https://www.linux.com/tutorials/advanced-dnsmasq-tips-and-tricks/